- 11 Nov 2025
- 1 Minute to read
- Print
- DarkLight
- PDF
Turbo360 BAM APIs
- Updated on 11 Nov 2025
- 1 Minute to read
- Print
- DarkLight
- PDF
Introduction
In Turbo360, APIs can be used if the user wants to use frameworks other than the .Net Library.
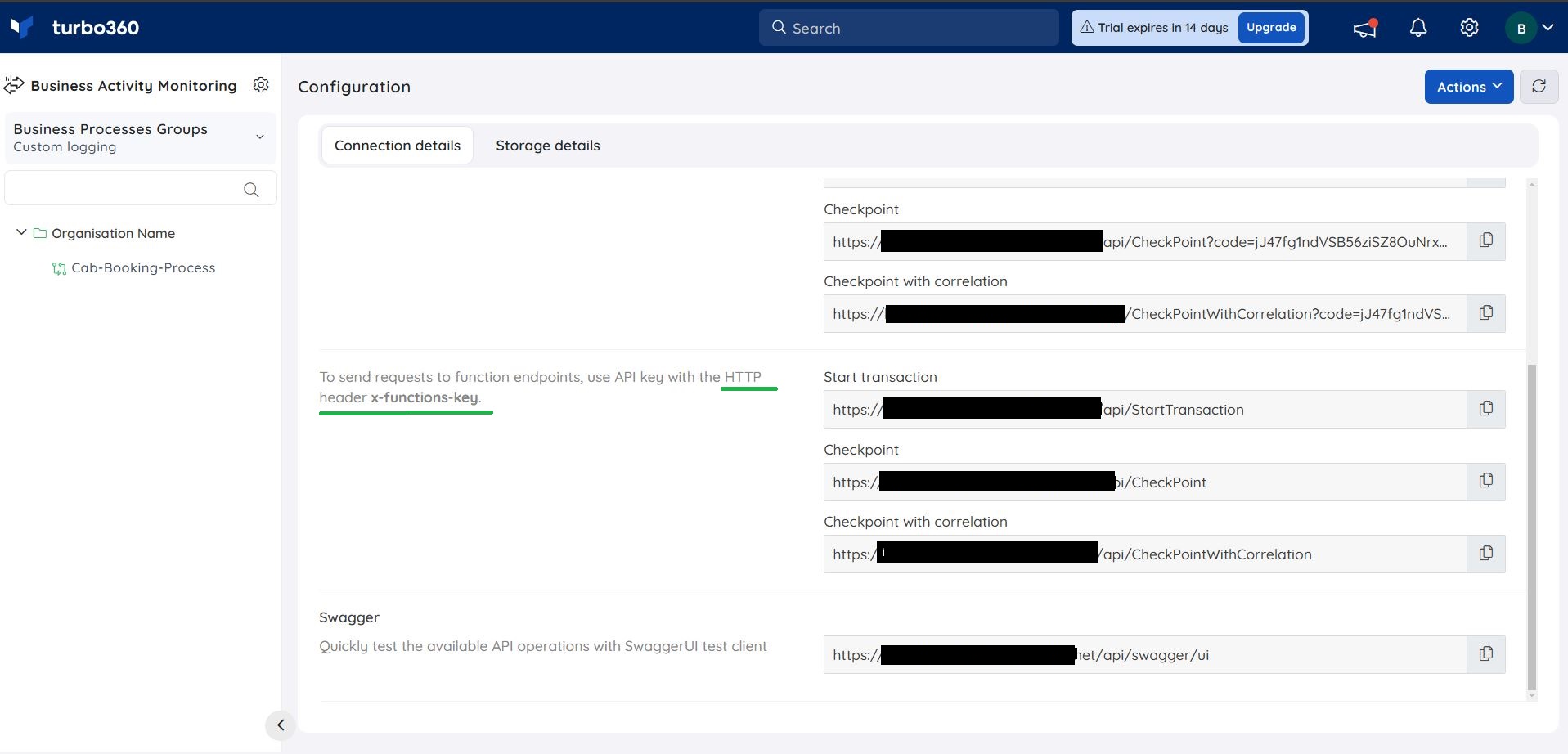
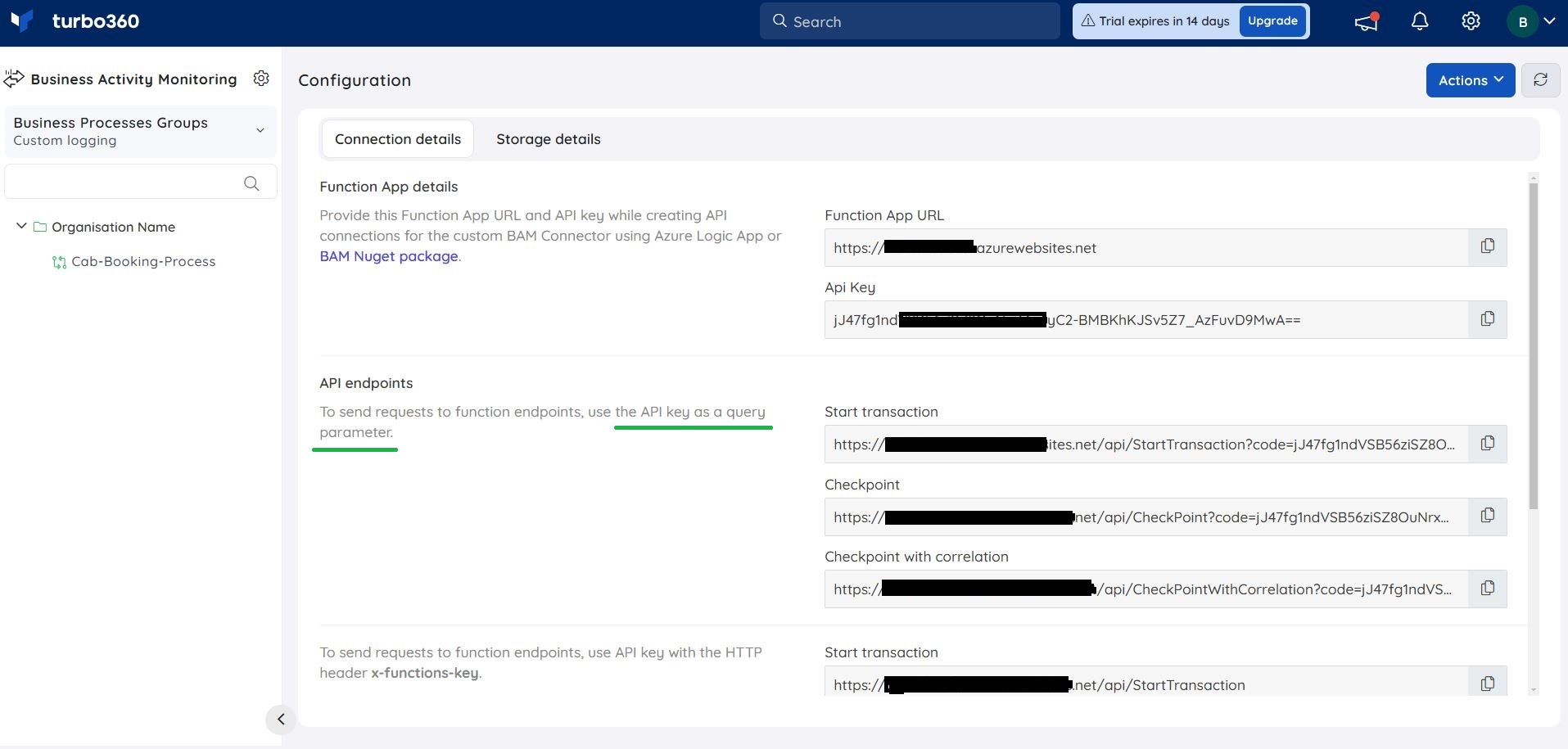
Users can hit the API with the help of URLs available in the Individual Endpoints section present in the BAM Connection details blade.
A Function App in Business Activity Monitoring has three functions:
Start Transaction
CheckPoint
CheckPoint with Correlation
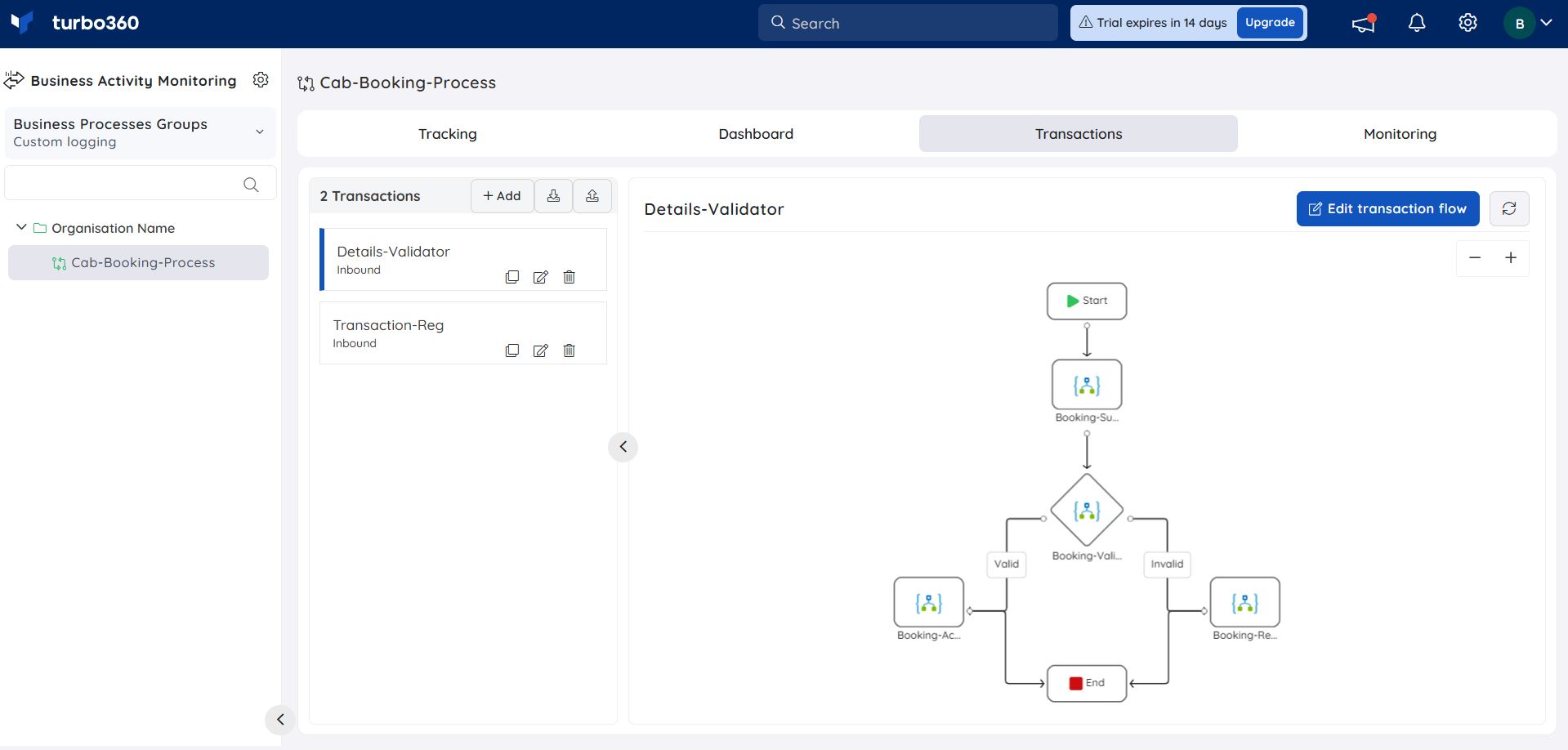
The business transaction will be plugged with Business Activity Monitoring as shown in the below image:
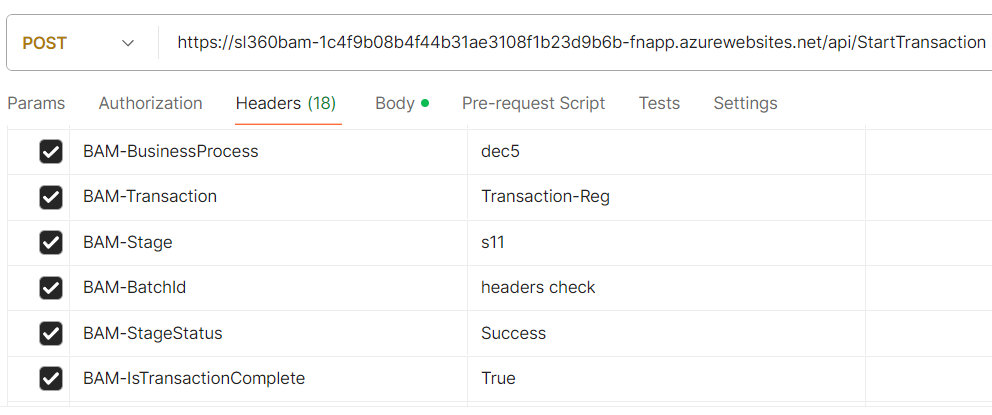
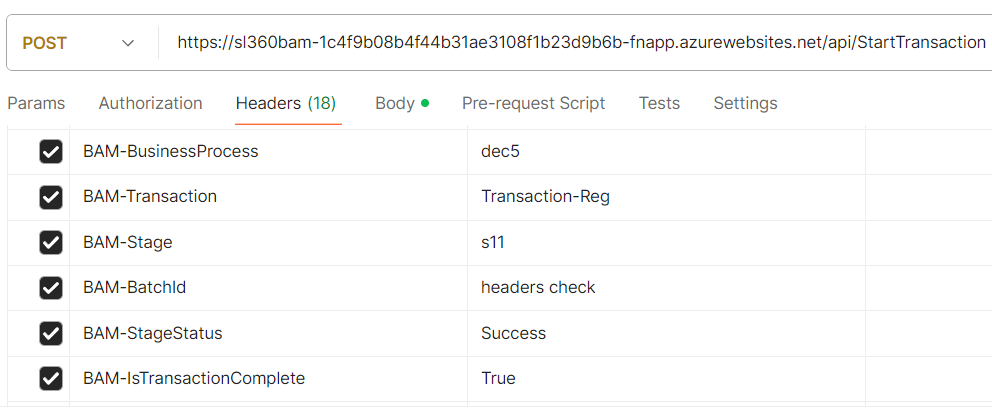
Users have to Start a Transaction with a Post URL that can be obtained from Actions -> BAM Connections Details under the Individual Endpoints section with Headers and Body as shown in the below image.
There are two ways to access Business Activity Monitoring using Exposed APIs:
1. Individual endpoints with key as a Header
2. Individual endpoints with key as a Query parameter
Triggering a Transaction Instance
Type 1: Key as a Header
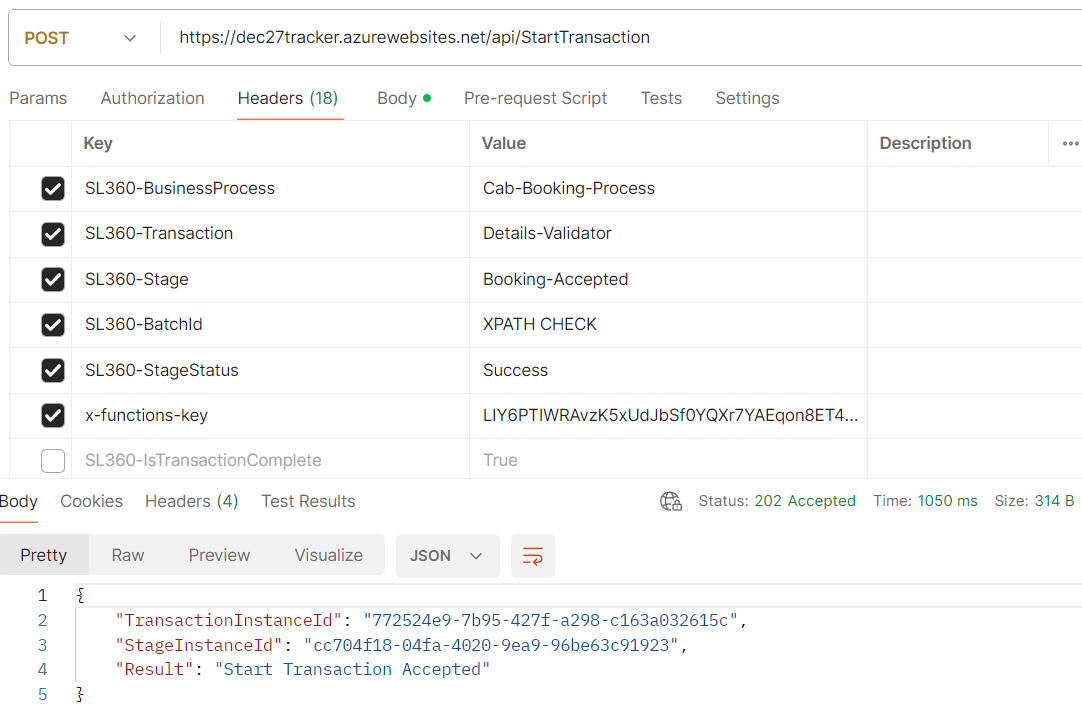
Type 2: Key as a Query parameter
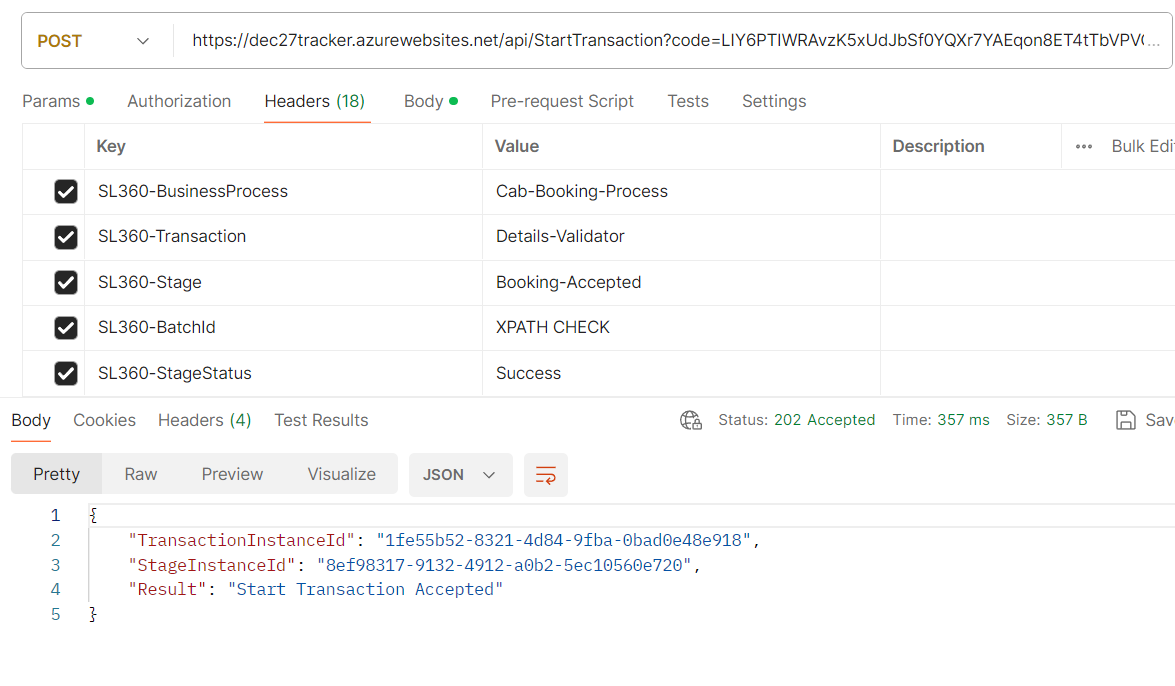
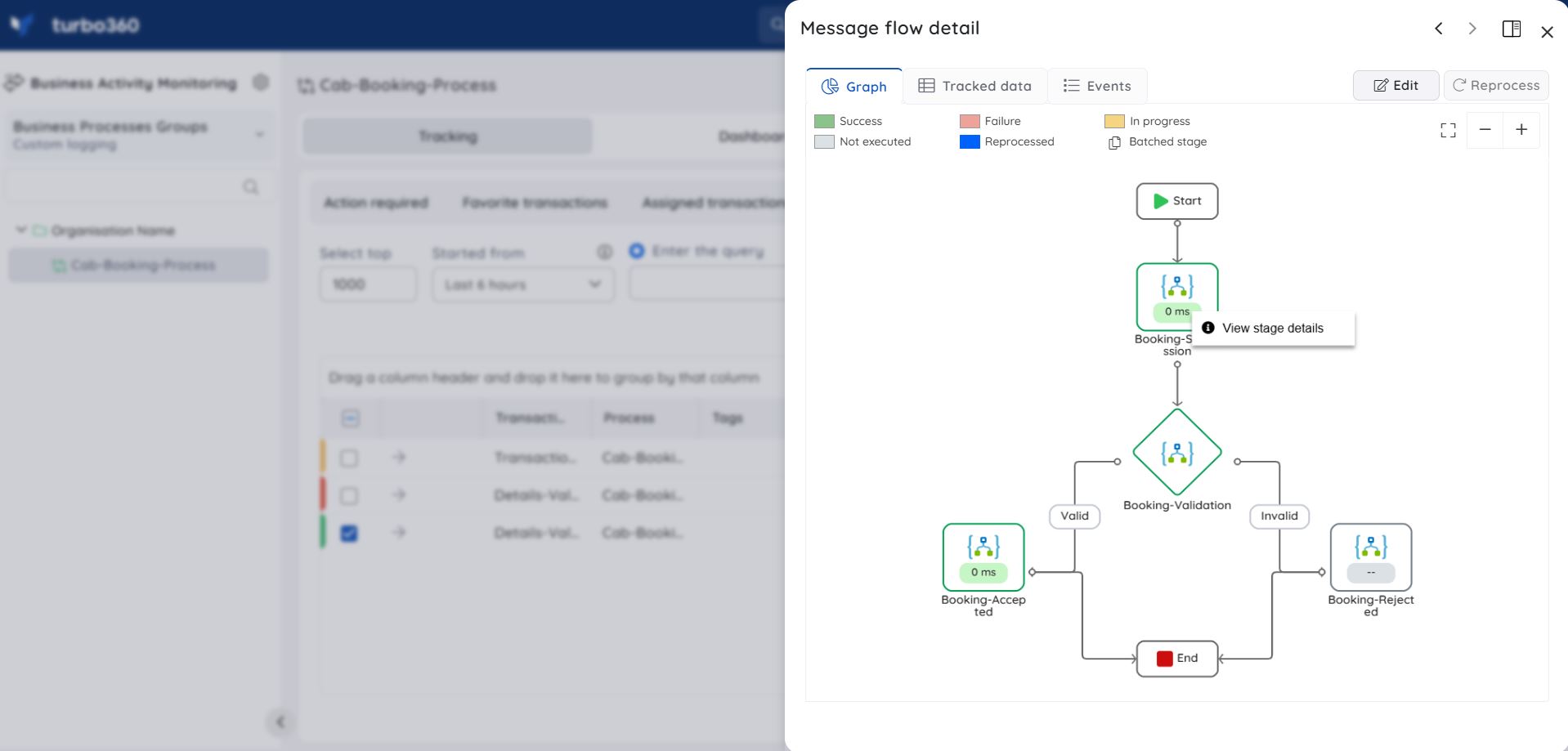
Take note of the TransactionInstanceId returned as an HTTP response in Start Transaction; it will be used in subsequent Checkpoints to indicate that it is the same transaction instance and not a new one.
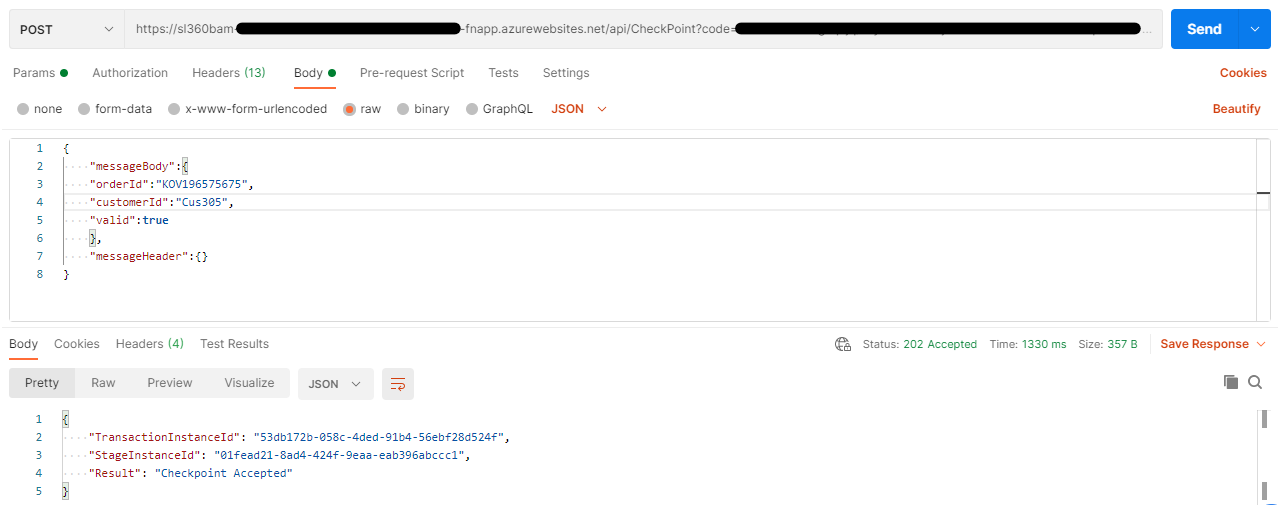
The next step is Configuring Checkpoint with Post URL with Headers and Body as shown in the below image.
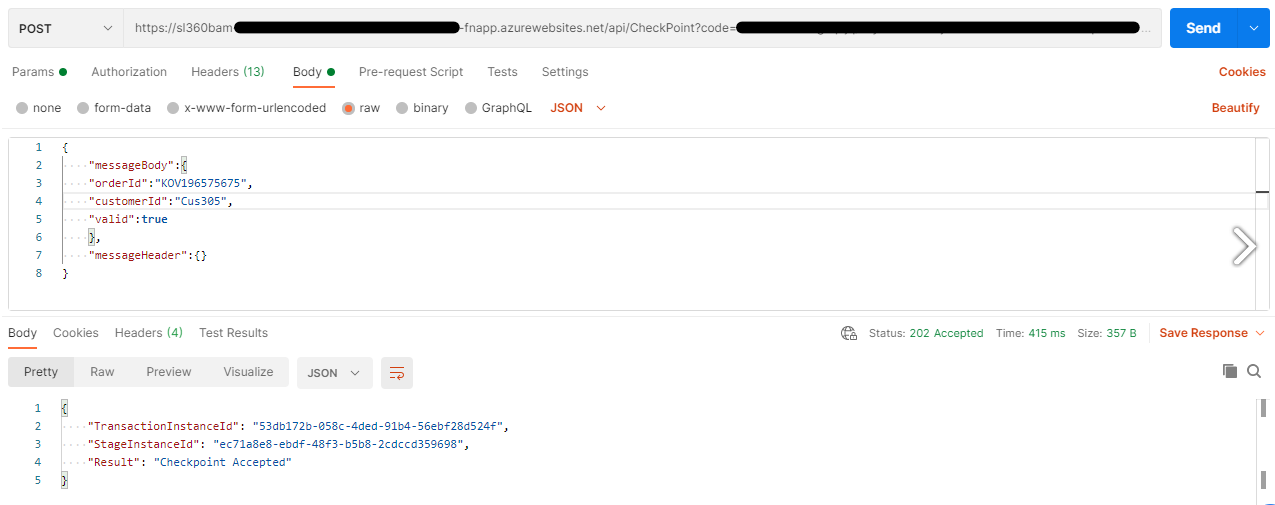
For the next checkpoint, the same Transaction ID must be used. The BAM-IsTransactionComplete header will be set to true because the transaction has come to an end.
Finally, the transaction will be tracked in Turbo360 Business Activity Monitoring.