- 07 Aug 2024
- 6 Minutes to read
- Print
- DarkLight
- PDF
Understanding how Entra ID SSO works
- Updated on 07 Aug 2024
- 6 Minutes to read
- Print
- DarkLight
- PDF
Turbo360 is can be deployed as both a SaaS and Private Hosted application.
When it comes to authentication, you can use one of 2 different schemes:
- Email/Password
- Entra ID single sign on
If you choose to use Entra ID single sign on then this page will describe how this works and what happens in your Entra ID tenant.
What does the Authentication Flow look like
When you authenticate from Turbo360 with Entra ID then the below image shows what the flow will look like.
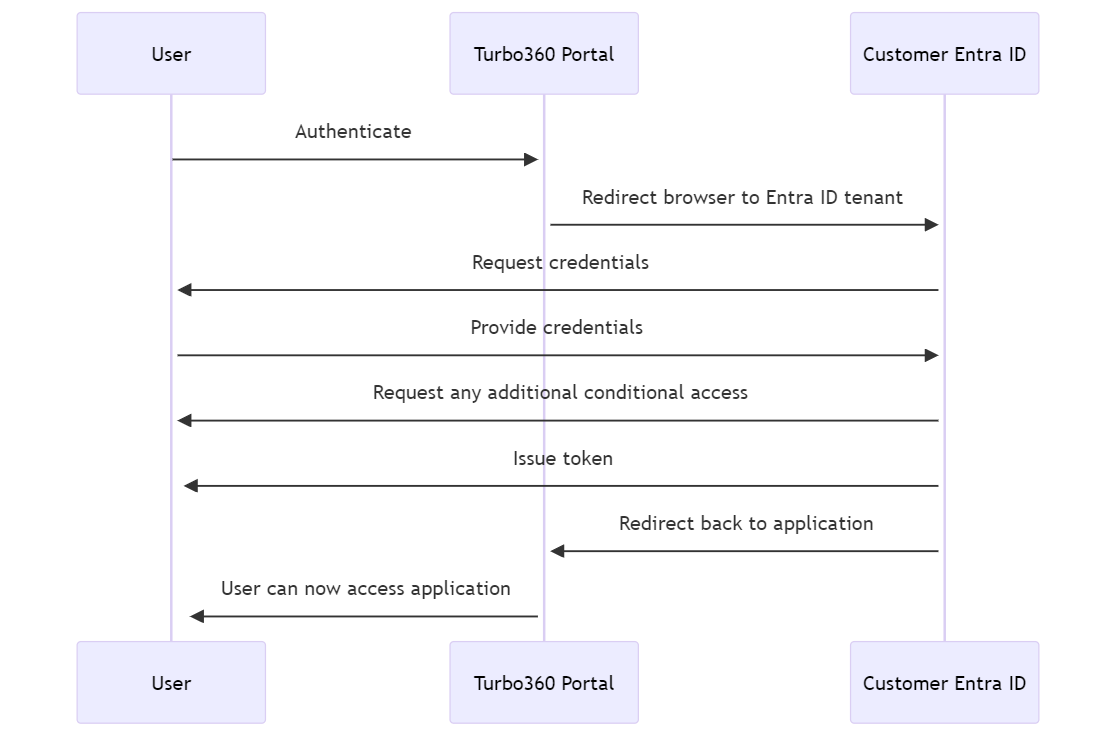
In summary the users browser will be redirected to Entra Id where the user will provide credentials, from where a token will be issued. The users browser is then redirected back to the Turbo360 application and the user can now access the application.
What will exist in my Entra ID tenant after we configure SSO
Turbo360 authentication is a multi-tenant application published by Kovai in the typical Entra Id manner. When a customer wants to configure their account or private hosted instance of Turbo360 to use Entra ID for SSO then you would be redirected by Turbo360 to your local Azure Entra ID Tenant. From here you will be asked by Entra ID to provide a consent to using the Turbo360 application. We are assuming that the person configuring Turbo360 to use Entra ID for SSO is someone with appropriate permissions on the customer Entra ID tenant to provide consent. In most cases this will be a global administrator.
When the consent is provided then Entra Id will create an Enterprise Application in the customer Entra ID tenant which will match the application published by Kovai. It will look like the below application:
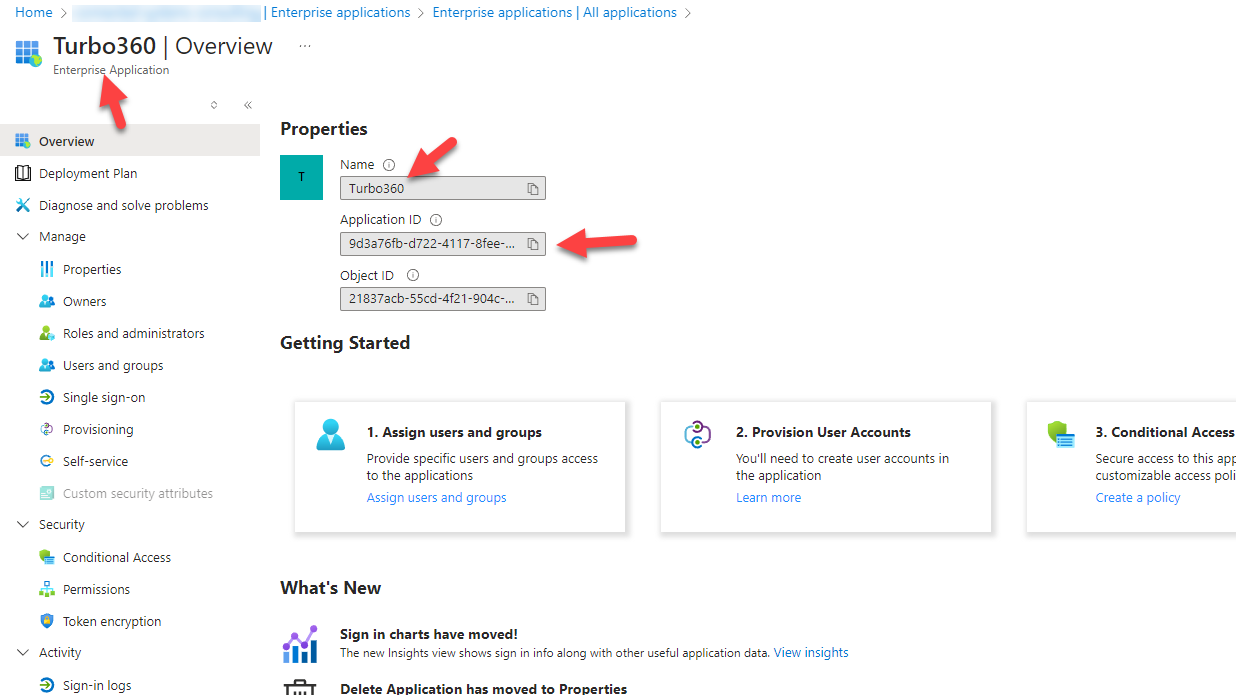
If you then go to the Permissions blade on the Enterprise Application you can see the permissions that the administrator consented for.
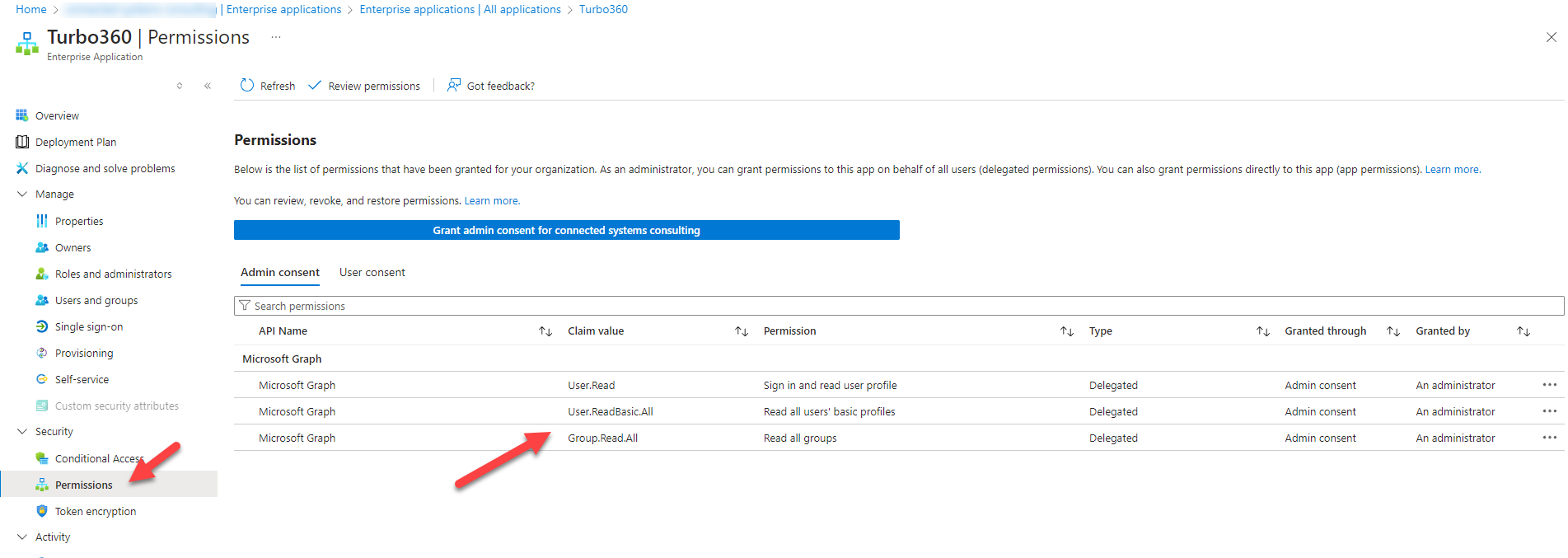
These permissions are used in the application when you want to add users to Turbo360. In Turbo360 you can choose a user or group from Entra ID and then you can add them to have permission to access modules within turbo360. The permissions assigned above allow Turbo360 to search for a user you wish to add.
At this point all of the other settings are the default settings for the Enterprise Application.
How do I setup Entra ID SSO
If you want to setup Turbo360 with Entra ID SSO then you can use one of the 2 pages below depending on if you are setting it up for the first time or if you have already configured Turbo360 with email/password authentication and then want to switch it.
Why do I need an Admin Permission
When setting up SSO with Entra ID a user who has appropriate permissions on your Entra ID tenant is required to perform these steps because the Admin Consent on the Entra ID side requires those permissions.
If it is a first time setup then you can get the Global Admin to be the person who registers the Turbo360 account.
If you are switching from Email to Entra then you can add the Global Admin as an Owner in Turbo360 from where they will be able to perform the switch.
What if I want to do the Entra ID actions outside of Turbo360
If you have a seperation of concerns between your teams and you would like to have the Entra Admin perform the setup step just on Entra ID and keep Turbo360 responsibility in a separate team then it is possible to do this.
When performing the action to configure Entra ID which creates the Enterprise Application then all that really happens is that Turbo360 redirects the browser to Entra ID with the right parameters to setup the Enterprise Application in the customers Entra Id tenant.
It is possible for the Entra ID Admin to put the url directly in their browser so that they would then provide the consent. At this point the Entra ID Admin does not need to be a user in Turbo360.
Once they have consented the application then the Turbo360 user can just do actions on the Turbo360 side. The steps for this would be:
Entra ID Admin
- Take a copy of the below url and modify the token {{Your-Tenant-ID}} to replace it with the guid that is the tenant id for your Entra ID tenant.
https://login.microsoftonline.com/{{Your-Tenant-ID}}/v2.0/adminconsent?client_id=9d3a76fb-d722-4117-8fee-3e95077a8c3f&scope=https://graph.microsoft.com/User.Read https://graph.microsoft.com/User.ReadBasic.All https://graph.microsoft.com/Group.Read.All &redirect_uri=https://portal.azure.com
If you would like to know a little more about the url, the key bit is the client_id matches the guid for the multi-tenant application that Kovai have published in Entra Id which needs to be the same guid as the Enterprise Application created in the customers local Entra ID tenant.
- User.Read
- User.ReadBasic.All
- Group.Read.All
The redirect url will mean that after providing consent the admin will be redirected back to the Azure Portal.
- The admin will put the url in their browser and they will be taken to Entra ID and asked to provide a consent as shown below.
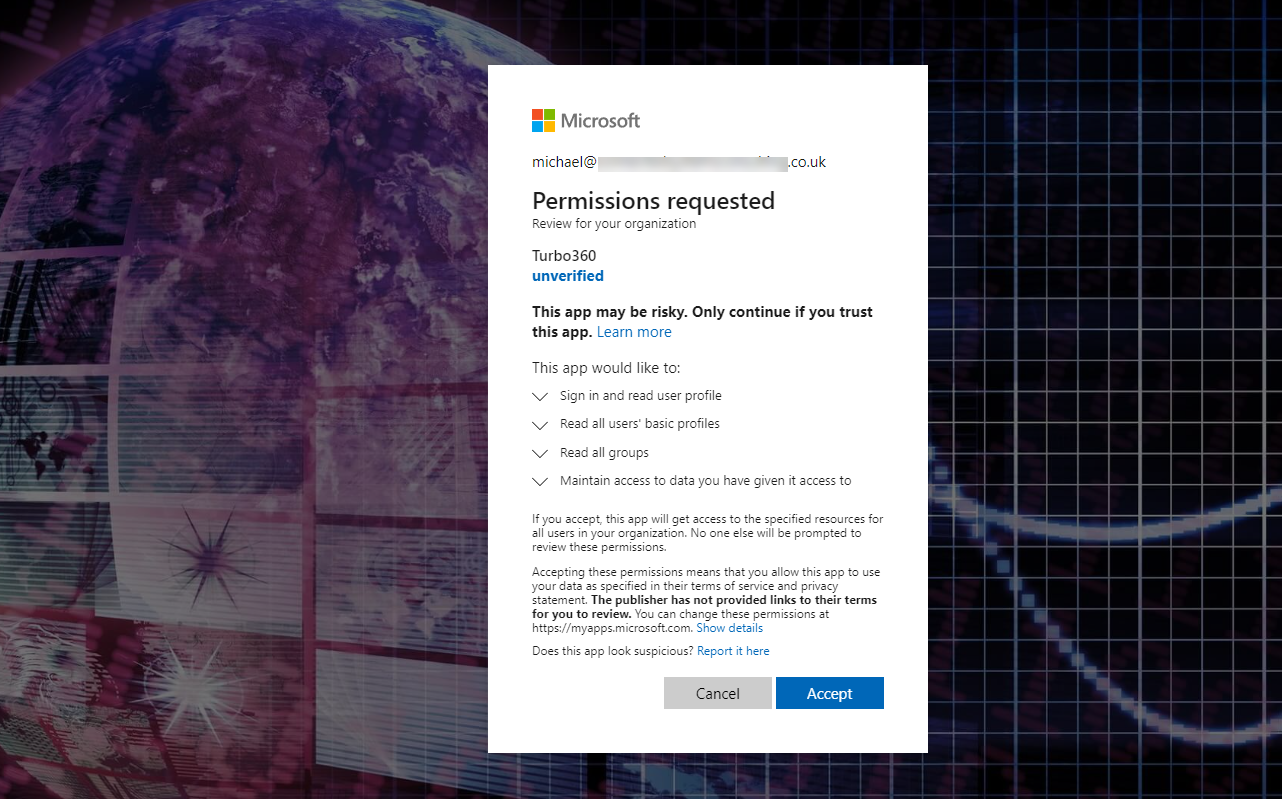
- When the admin clicks Accept then the Enterprise Application will be created in the Entra ID tenant and the permissions granted as described earlier in this page.
At this point the Entra ID Admin tasks are complete and they can hand over to the Turbo360 user.
Turbo360 User
The tasks for the Turbo360 User depend on if you are signing up for the first time or changing the authentication from email to SSO. You can follow the steps in either of the 2 pages below but the key differences are that you do not need to be a Global Admin on Entra ID. You just need to be an owner of the Turbo360 account. When you redirect to Entra ID you will not be prompted to provide consent because your Entra ID Admin already did this.
Please note when you are doing this setup separately without the fully automate experience, please check with the Turbo360 team if you are a private hosting customer as we may need to register your private hosting url for SSO if these steps are performed by separate people.
Follow one of the 2 pages below:
When you complete the process you should be able to login with Entra ID and also add new users and groups and configure their permissions within Turbo360.
Additional Notes for Entra ID Admin
Because Turbo360 authentication will be using SSO with your Entra ID and we are using an Enterprise Application for authentication. There will be a number of features you can take advantage of if you want to leverage then.
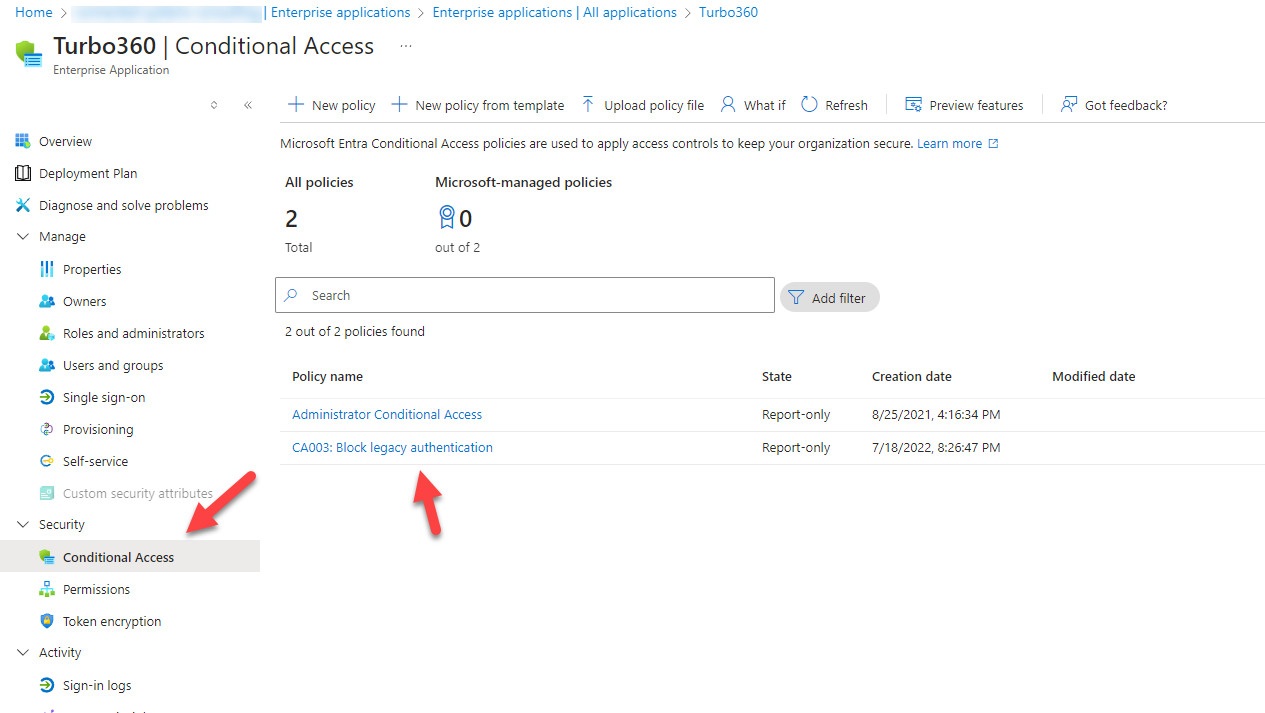
Conditional Access Policies
If you are using conditional access policies in your Entra ID tenant you will be able to apply these to Turbo360 in the same way you do for your other applications. Examples you might choose could be things like:
- Enforce MFA
- Enforce safe locations
- Limit risky user access
Below you can see where you would use these:
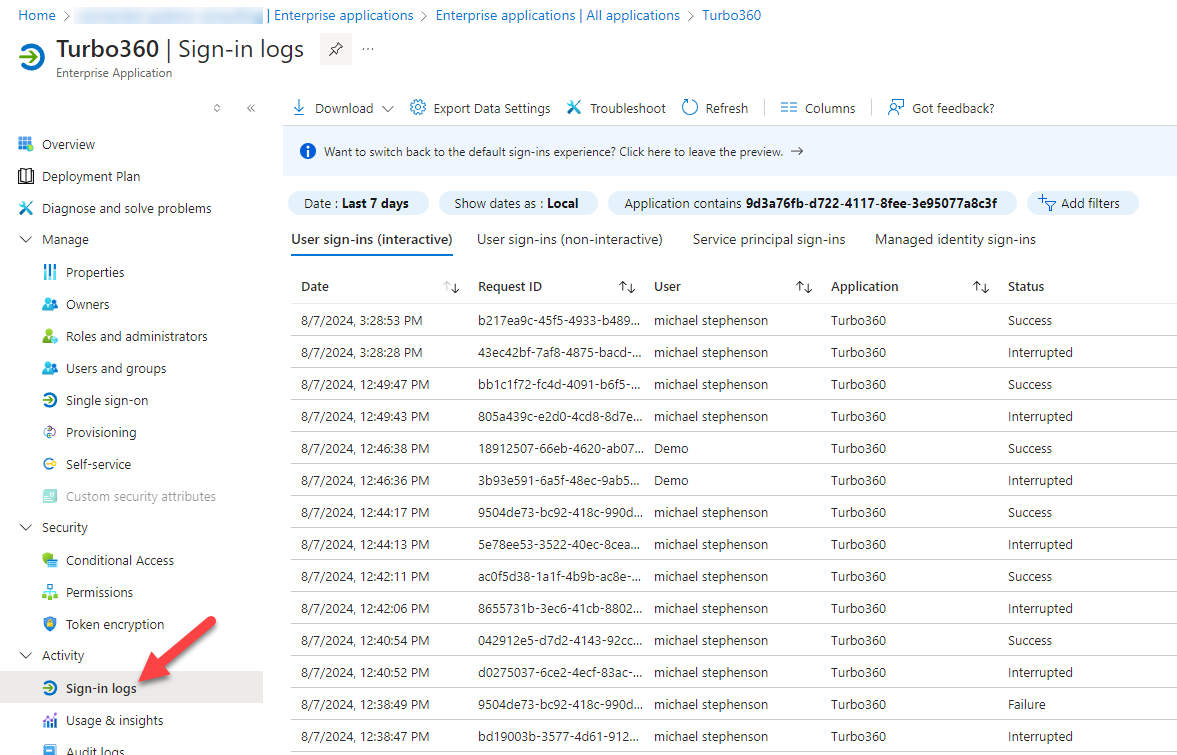
Entra ID Sign In Logs
When users are authenticating then you will have the normal sign in logs in Entra ID available if you want to use then yourself or integrate them with a SIEM solution.