- 19 Nov 2024
- 4 Minutes to read
- Print
- DarkLight
- PDF
What is Service Principal?
- Updated on 19 Nov 2024
- 4 Minutes to read
- Print
- DarkLight
- PDF
Introduction
Service Principal is an application within Microsoft Entra ID, which is authorized to access resources in Azure. This access is restricted by the roles assigned to the service principal, giving you control over which resources can be accessed and at which level.
Turbo360 uses the authentication tokens of the Service Principal to manage the resources, this is achieved by associating the Azure Service Principal with necessary permissions.
These permissions are restricted to exactly what Turbo360 can do.
The necessary activities to perform such restrictions include:
- Create a Service Principal.
- Authorize and Assign a role to the Service Principal.
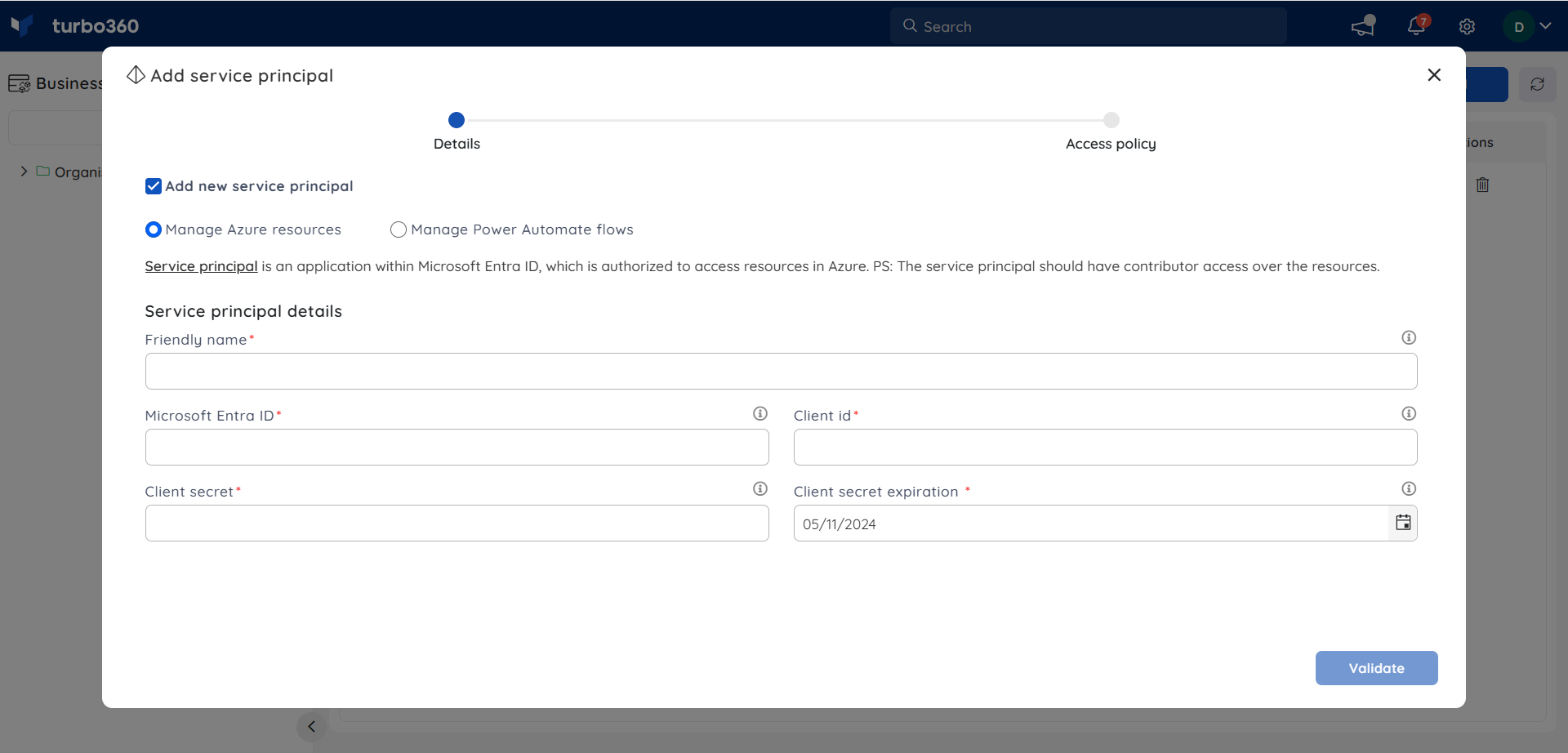
To associate a Service Principal with Turbo360, the following values are required:
- Microsoft Entra ID - Tenant directory Id.
- Subscription Id - The Subscription Id of the Azure Subscription in which the resource exists.
- Client Id - Id of the Service Principal object / App registered with the Microsoft Entra ID directory.
- Client Secret - Application password.
These values can be collected from the Azure portal in the following way.
Create a Service Principal
- Navigate to the Microsoft Entra ID tab in the left side menu in the Azure portal and click App registrations.
- Click on the New registration button.
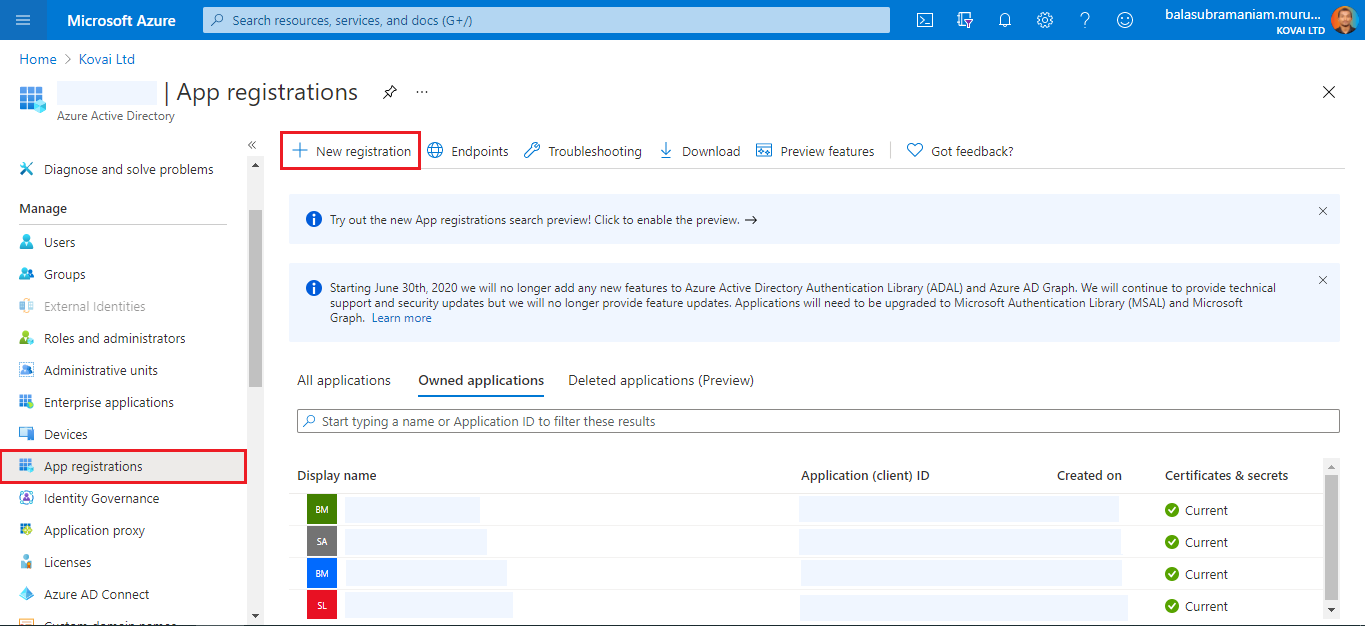
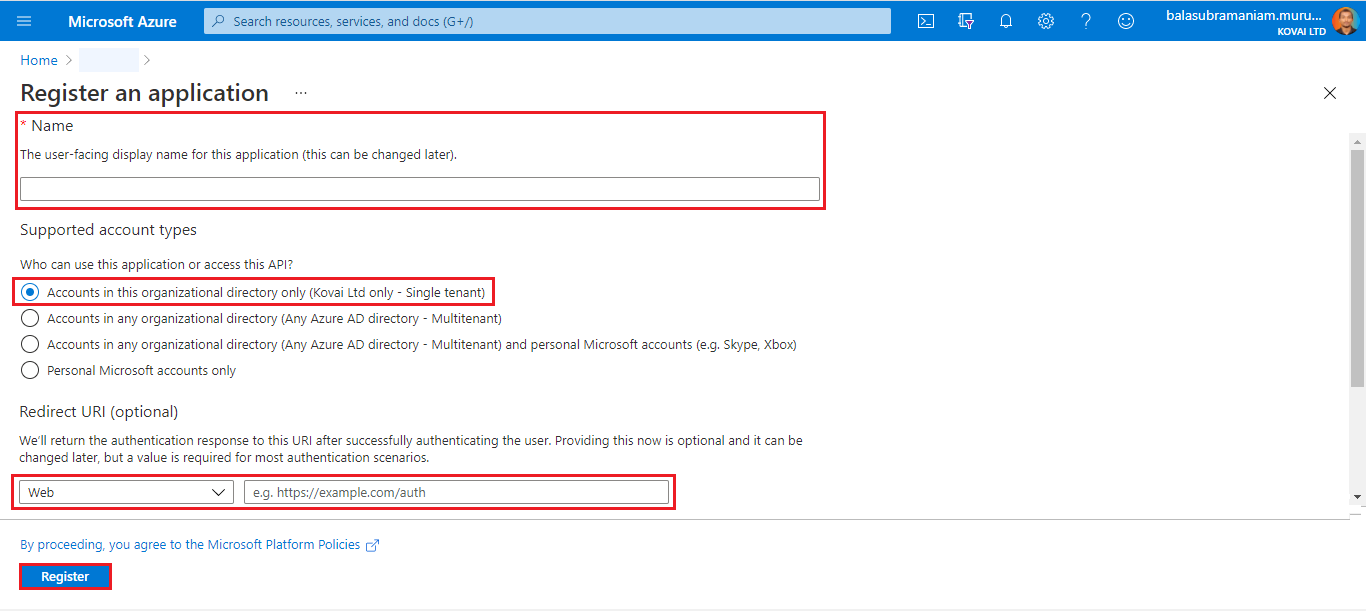
- Provide a Name for the Service Principal. Select a supported account type, which determines who can use the application. Under Redirect URI, select Web for the type of application that needs to be created. Enter the URI to which the access token is sent. Click on the Register button.
- Once the Service Principal is created successfully, it will be listed in the App Registration grid.
Get Azure Tenant ID
In Azure Microsoft Entra ID, a tenant is a representative of an organization.
It is a dedicated instance of the Azure Microsoft Entra ID service that an organization receives and owns when it creates by signing up for a Microsoft Azure account.
Each Microsoft Entra ID tenant is distinct and separate from other Microsoft Entra ID tenants.
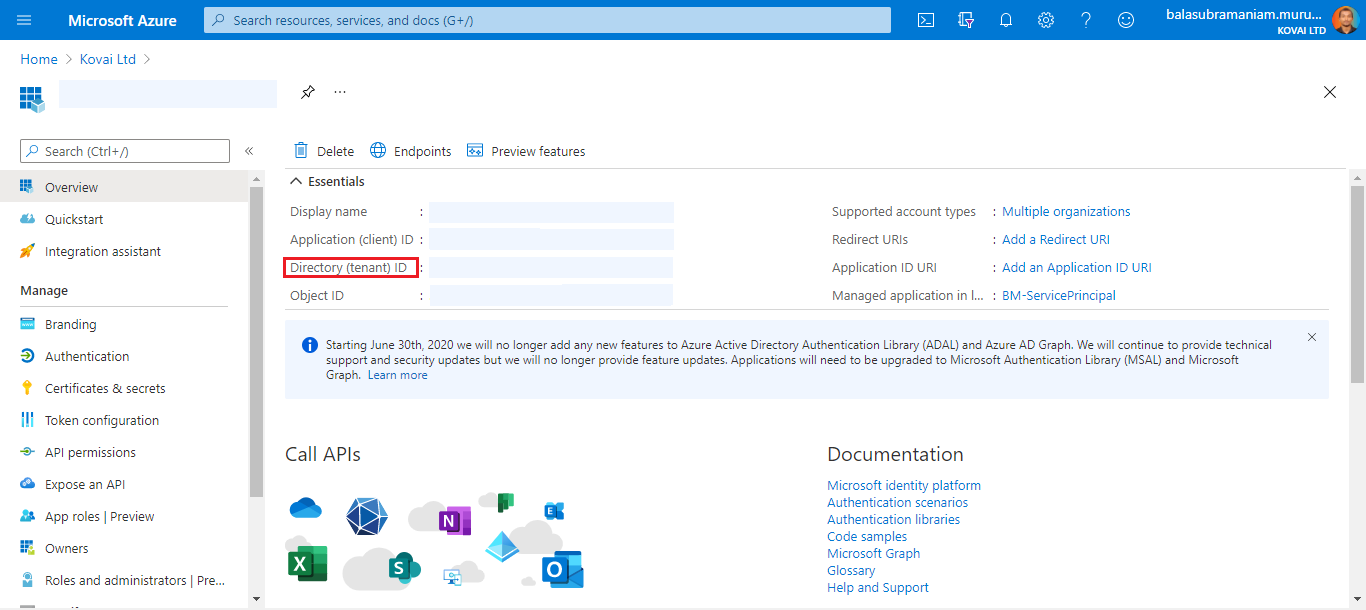
- Click on the name of the Service Principal.
- The required Tenant Id is the Directory (tenant) ID from the Essentials section.
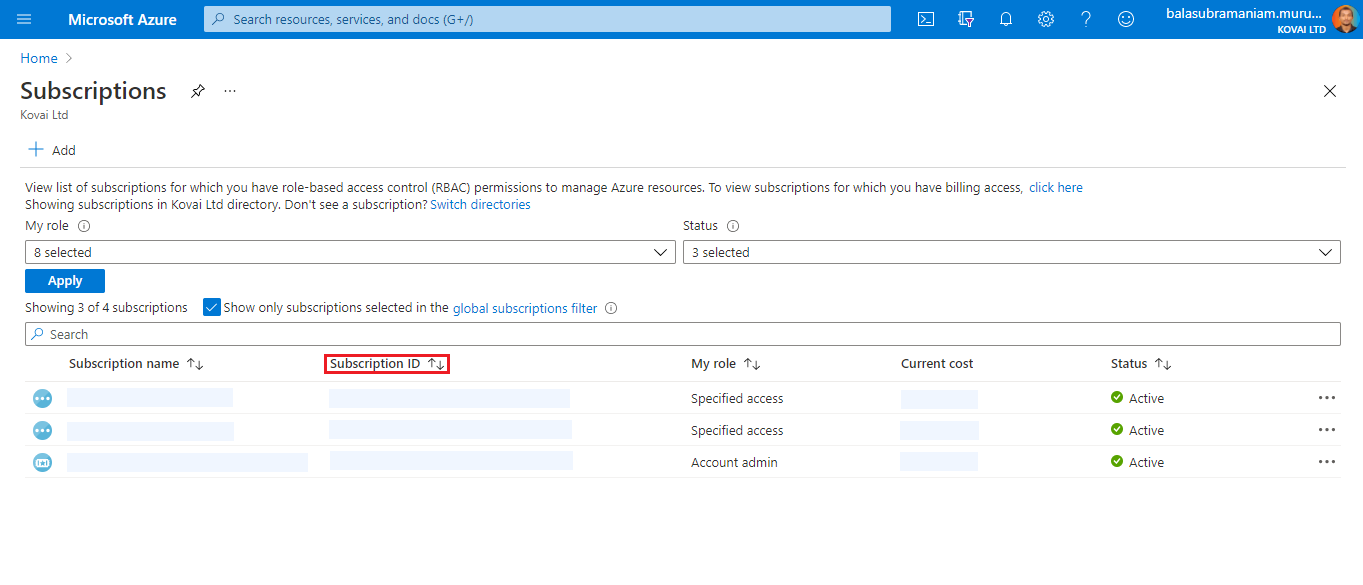
Get Subscription ID
A Subscription ID is a GUID that uniquely identifies a Subscription.
- Navigate to the Subscriptions tab in the left-side menu.
- All the subscriptions will be listed in a grid. Copy the Subscription Id (where all the desired resources are present) from the Subscription ID column.
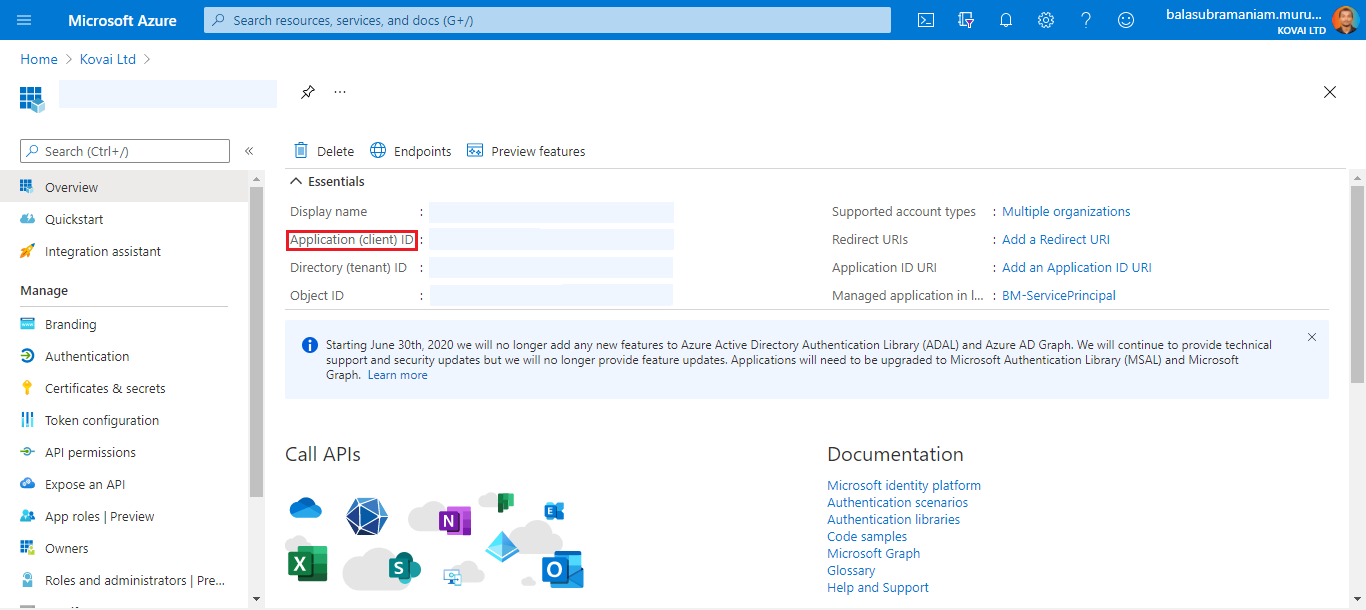
Client ID and Client Secret
A Client ID is a 16-character string that represents the application.
- Click on the name of the Service Principal.
- The required Client Id is the Application (client) ID from the Essentials section.
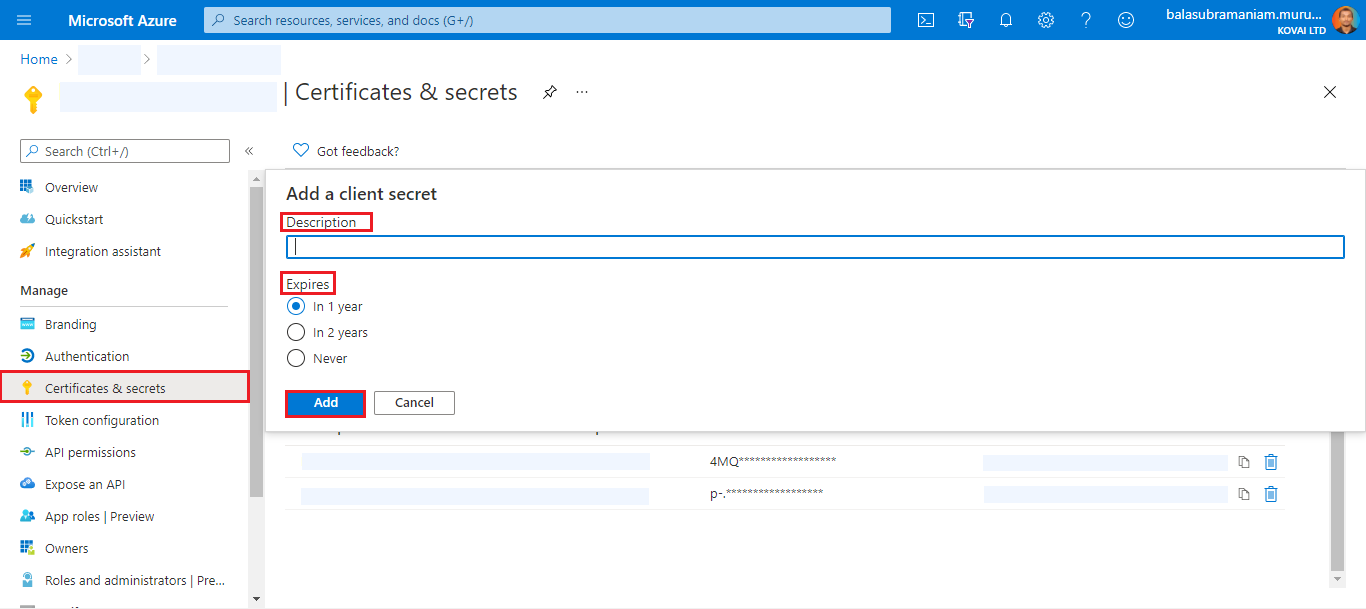
Secret key is a security key that Windows Live ID uses to encrypt and sign all tokens. It is used by the application to prove its identity when requesting a token.
- Click on Certificates & secrets under the Manage section from the left pane.
- Click on New client secret, provide the Description and Expiry time, and click Add.
- Once saved, it will show the Client Secret. This Key will only be shown once. This value should be copied and saved.
Authorize Service Principal and Role Assignment
To access the resources in a subscription, the application must be assigned to a role. The right permissions for each role are defined based on different use cases. The scope of the application can be set at the level of the subscription, resource group, or resource.
Permissions are inherited to lower levels of scope. For example, if an application has the Contributor / Owner role for a resource group, it can access the resource group and any resources it contains.
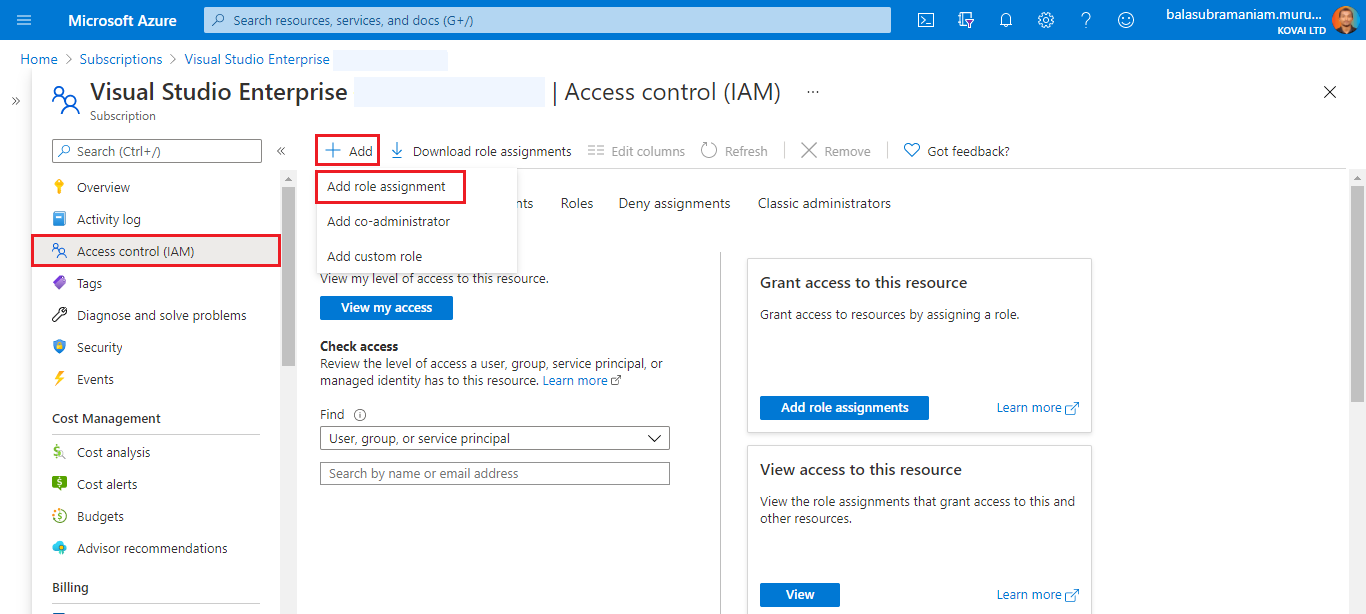
To authorize the service principal to access a Subscription:
- Navigate to that Subscription. Click on Access control (IAM).
- Select Add->Add role assignment.
- Switch to the Privileged administrator roles tab and choose Contributor.
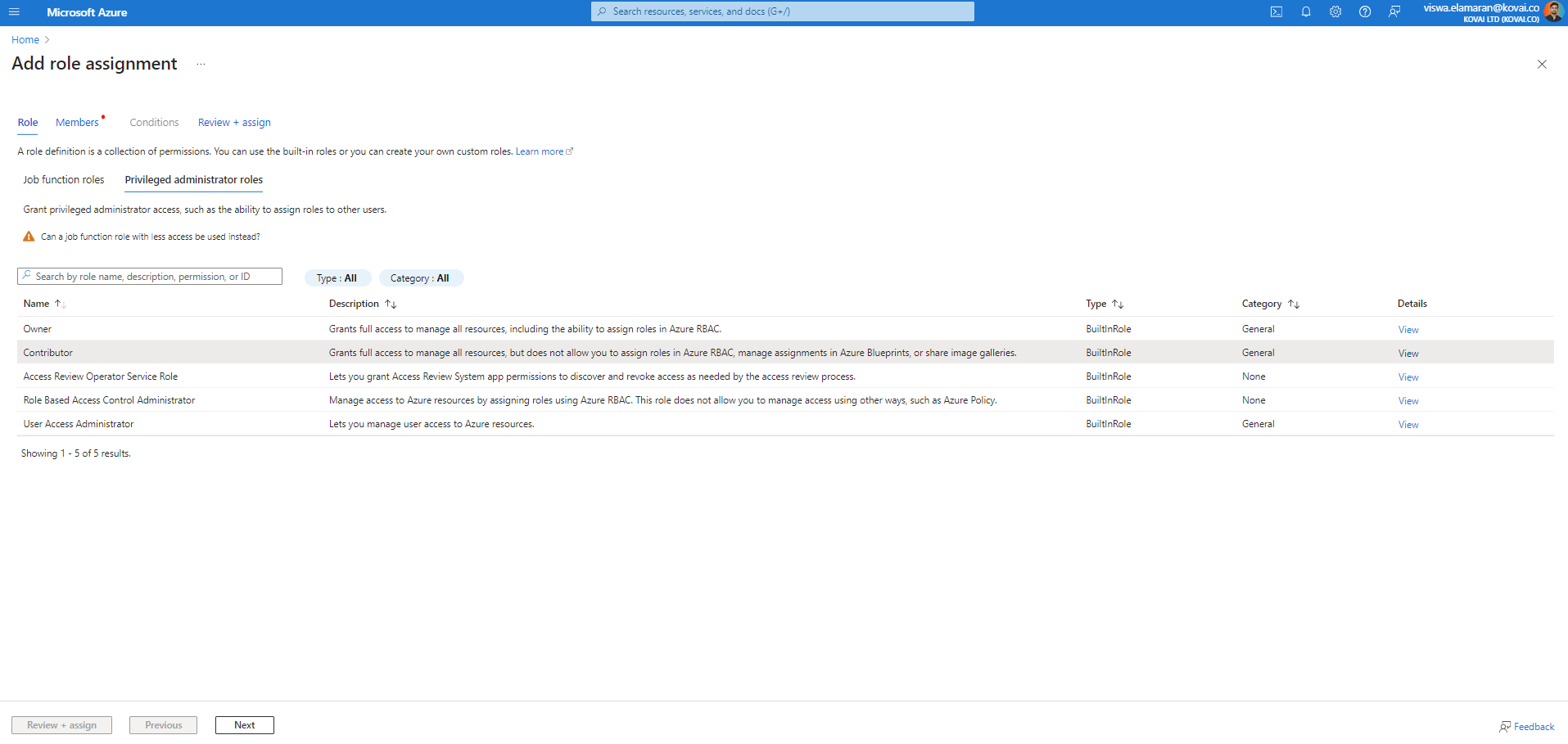
- Clicking Next will proceed to the role assignment screen. Choose User, group, or service principal option for the Assign access to field.
- Multiple service principals can be assigned with the specified role acess for the relevant Azure Subscription by selecting them as its Members.
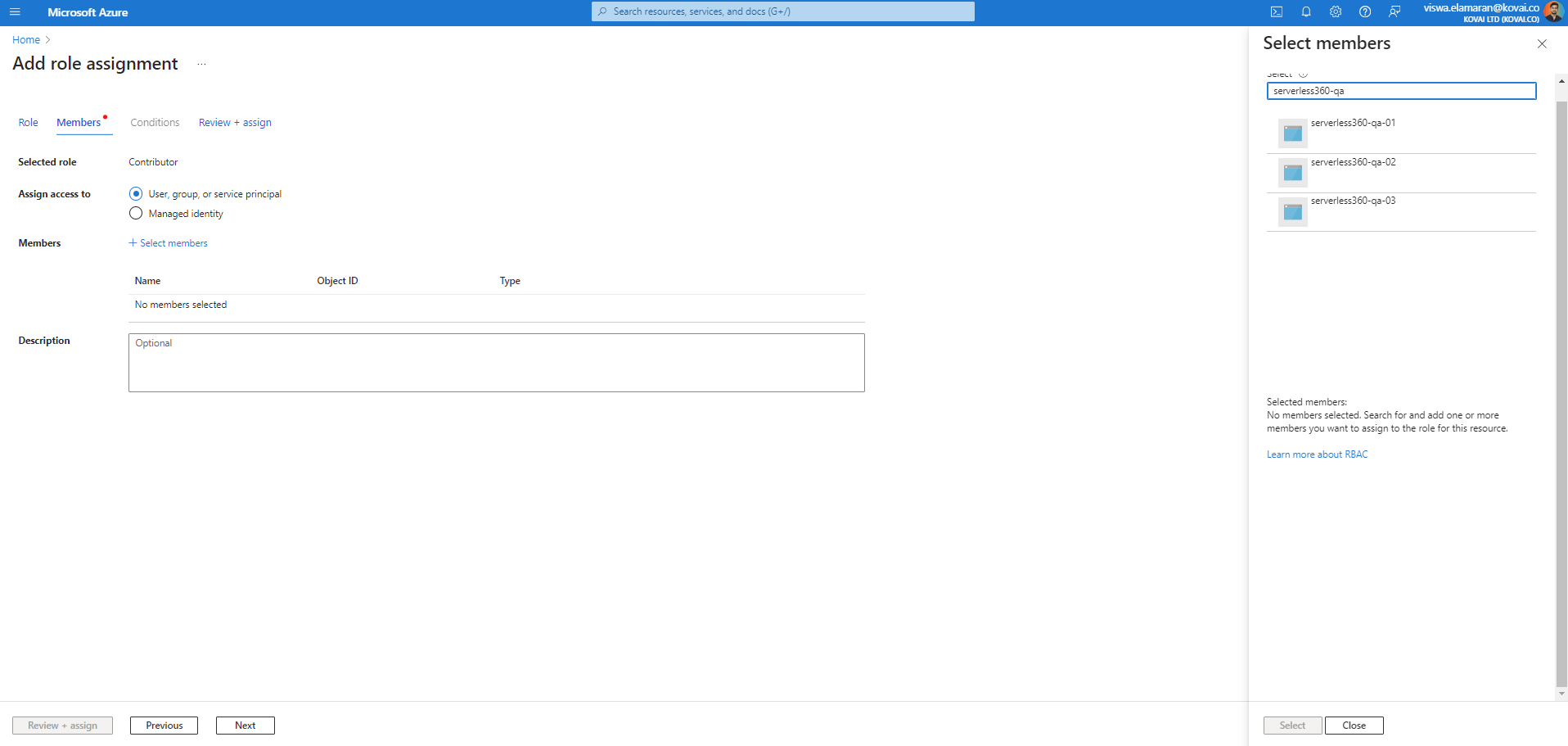
- Click Review+assign to review and save the role assignment.
It may take some time for the above configurations to take effect.
Why does Turbo360 need Contributor access for the Service Principal?
Turbo360 has got capabilities to manage and monitor Azure resources. We need to access the resources in their subscription and perform operations on them. The required permission to achieve these capabilities is Contributor access. With this access, it can access the resource group and any resources it contains.
If the contributor access is not given, the users can only view the resources that are listed in Turbo360 but cannot perform any operations or monitor them.
Please refer to this Microsoft documentation
Now the created Service Principal can be associated with Turbo360.
To know more about Service Principals and the above process, read the following articles from Microsoft:

